Learn about DMARC, SPF, and DKIM
Welcome to DMARCPal's Learn blog. Check our posts to discover and learn more about DMARC, SPF, DKIM, and how to get the most value of your DMARCPal subscription.
Short answer: deploy ARC where mail is actually being forwarded or transformed.
That usually means the forwarder, mailing list, or gateway should do the sealing. The final receiver should do validation and trust decisions. A domain owner that only sends direct mail usually does not get much benefi...
If DMARC looked perfectly healthy yesterday and suddenly starts failing for forwarded messages or list traffic, you are not looking at a weird edge case. You are looking at a normal email path.
Forwarders and mailing lists are exactly where DMARC gets interesting, because they change message paths...
If ARC still feels fuzzy, that is completely normal.
Most admins first meet ARC while debugging a very practical problem: "this message is legitimate, but DMARC failed after forwarding." ARC exists for exactly that kind of path.
ARC stands for Authenticated Received Chain. It is defined in RFC...
When DMARC fails, the DNS record is often blamed first.
In practice, the fastest path to the real cause is usually the message header, specifically the Authentication-Results line. That one line tells you what the receiver believed about SPF, DKIM, and DMARC at evaluation time.
If this still f...
If a domain does not send email, that domain should still have an email authentication posture.
That sounds odd at first, but parked or unused domains are frequent spoofing targets precisely because nobody watches their mail flow. Attackers can forge From: yourbrand@example.com from a quiet doma...
pct looks like a comfort knob.
Set p=quarantine; pct=10, wait a bit, then raise it to 25, 50, 100. On paper that sounds controlled and safe.
In production, it is useful but not magical. Some receivers treat pct as a hint, sampling details vary, and policy behavior is not guaranteed to be...
Sometimes DMARC reports need to go somewhere other than the domain in the From address. That is common when reports are collected by a shared mailbox, a central security team, or an external processor such as DMARCPal that receives and organizes reports. DMARC allows that, but only after the destina...
At some point every DMARC rollout hits this exact moment:
"The DNS record is published... now what?"
The answer is reporting. Specifically aggregate DMARC reports (rua) sent as XML files.
This is where DMARC stops being a checkbox and becomes operations: figuring out who is sending as exa...
DMARC reporting is where the whole thing stops being theoretical.
If DMARC is the policy you publish in DNS, DMARC reports are the receipts: mailbox providers telling you what they observed when mail claiming to be from example.com hit their systems.
Those reports are what let you answer que...
If email keeps landing in Gmail's Promotions tab, the instinct is to look for a technical switch: "maybe DMARC fixes this".
DMARC is worth doing, but it's not that switch.
DMARC is about whether a message is allowed to claim a domain in the visible From: address. Gmail uses that (and SPF/DKI...
If email from a perfectly legitimate system suddenly starts landing in spam (or bouncing), it usually isn't because "deliverability is mysterious".
It's because mailbox providers have been steadily raising the floor for what counts as a well-behaved sender.
This isn't just about inbox placement,...
“Apex domain” is one of those phrases that sounds more exotic than it is.
In day-to-day DNS work, the apex is simply the top name of the zone being edited. If the DNS zone is example.com, then the apex is example.com itself (sometimes shown as @ in DNS dashboards). If the zone is news.exa...
DMARC gets talked about like a single switch you flip for a domain.
In reality, most domains are a small ecosystem:
- the apex (
example.com) where people type addresses and expect mail to "just work" - a handful of subdomains used for actual sending (
news.example.com,billing.example.com,...
It only takes one look at a real DMARC record to realize why people hesitate.
p, sp, pct, rua, ruf, fo, ri, rf...
It's not hard once it clicks. It's just that every tag looks equally important when you're new to it, and DNS is an unforgiving place to experiment.
This is a fiel...
If you've ever stared at a DMARC report thinking "but SPF is passing... why is DMARC failing?", you've already met identifier alignment.
Alignment is one of those things that sounds like an academic detail until it bites you in production. Then it becomes the entire story.
In DMARC terms, what...
Email spoofing and phishing are two types of online scams that have become increasingly common in recent years.
While they may seem similar on the surface, there are important differences between these two methods of tricking people online. Understanding these differences is important to protect...
Forged emails are a growing concern for personal and business communication. With the ease of sending fake emails that appear to come from a different source, it's essential to be aware of the dangers and take steps to prevent them.
This blog post will explore the reasons why it's so easy to send ...
DMARC is a protocol for email authentication. It allows domain owners to specify how email from their domain should be authenticated. But some domain owners may get too many reports and want to stop receiving them.
Some people may want to stop receiving DMARC reports because they are getting too m...
This is a continuation post covering a process to setup DMARC on active domains. Visit A (sane) DMARC setup process for busy email domains to know more about this post series.
Mistakes can happen.
An updated DKIM selector record may be missing a semicolon. Someone in a rush could mistype t...
This is a continuation post covering a process to setup DMARC on active domains. Visit A (sane) DMARC setup process for busy email domains to know more about this post series.
In the previous steps of the 5-Stages DMARC Setup process we got to know more about the domain email traffic pattern...
This is a continuation post covering a process to setup DMARC on active domains. Visit A (sane) DMARC setup process for busy email domains to know more about this post series.
Depending on the volume of emails you send, how old your domain is, and how much exposure it has, your DMARC reports...
This is a continuation post covering a process to setup DMARC on active domains. Visit A (sane) DMARC setup process for busy email domains to know more about this post series.
The objective of this stage is to collect data so we get to know how email from the domain flows and, in parallel, m...
This is a continuation post covering a process to setup DMARC on active domains. Visit A (sane) DMARC setup process for busy email domains to know more about this post series.
Planning and controlling the DMARC deployment process is crucial to avoid problems and questions down the road that...
This is a continuation post covering a process to setup DMARC on active domains. Visit A (sane) DMARC setup process for busy email domains to know more about this post series.
Here is a brief overview of the DMARC setup process we will be covering in this post series:
The 5-Stages DMARC Se
...DMARC is great. It allows you to publish your email sending policies, and those are used to prevent phishing emails using your domain. On top of that, it also provides reporting facilities that give you insights on your email delivery.
Implementing DMARC on new domains is straightforward. You just...
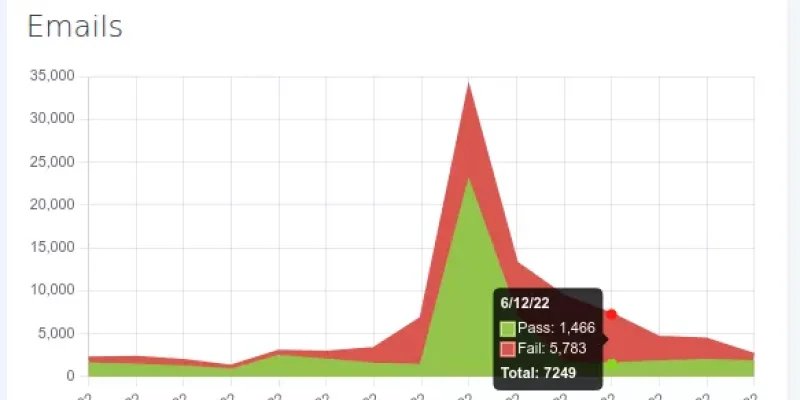
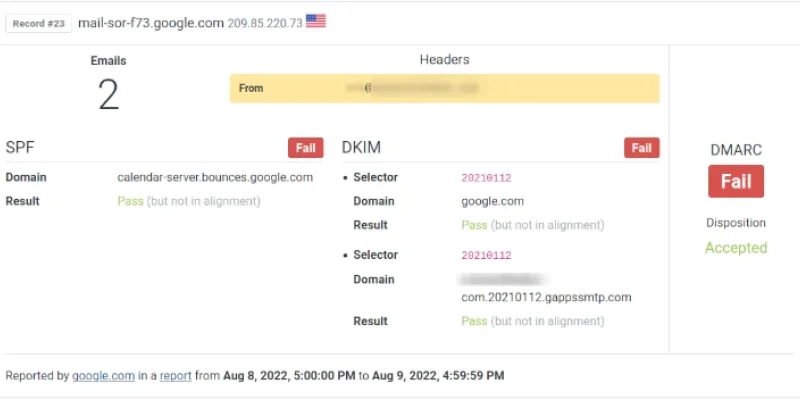
If you are a Google Workspace user and use Google Calendar, you may have noticed some DMARC fails on your DMARC reports.
Here’s a sample record extracted by DMARCPal Record Explorer showing the issue:
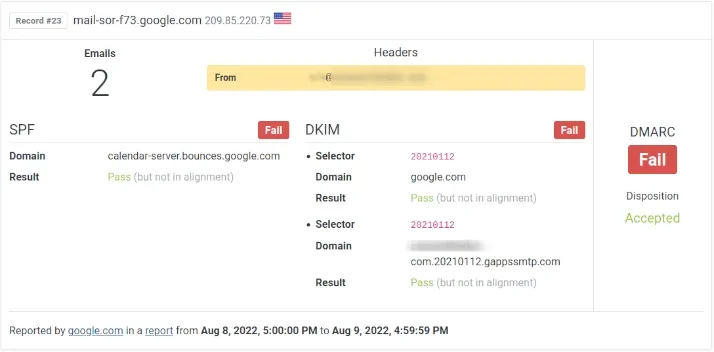
The problem is caused by Google sending those emails from domains that don’t align with the...
We’ve seen this happening to a few domains hosted on Google Workspace: DKIM is properly set up on the domain, email is okay, and DMARC passes.
All seems fine, except that DKIM is not authenticating emails “From” the user domain.
Because Gmail works, people think that DKIM is doing the right th...
Not a long time ago, Internet email was based on trust. Trust on the servers, trust on the people running the servers.
Trust that who you see in an email “From” is really who wrote that message.
As of 2020 about 3+ billion forged emails are sent in a day, and it is safe to say (no pun intended...
DKIM is short for DomainKeys Identified Mail. It is a mechanism to verify that some core information of an email message, such as its body, and the “From” and “Subject” lines, are authentic and haven’t been tampered with by someone while the email was in transit.
So when you send an email using...
By default, any computer connected to the Internet can send emails pretending to come from your domain.
That’s true. If you registered example.com for your business and just configured basic email (i.e for sending and receiving XXX@example.com messages), then someone on a cybercafe on the ot...
This happens more often than we think: an employee receives an email from his boss requesting him to do something.
It might be something as simple as requesting a document.
Or more serious, such as the credentials to the company’s social media accounts. Or to transfer several thousand dollars to...